Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
Sophos Firewall ciphers available in the Sophos Firewall for WAF
Strong ciphers
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030)
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f)
- TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 (0x9f)
- TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 (0x9e)
Weak ciphers
- Because CBC is used
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028)
- TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 (0x6b)
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (0xc027)
- TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 (0x67)
- Because SHA1 is used (in addition to CBC)
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014)
- TLS_DHE_RSA_WITH_AES_256_CBC_SHA (0x39)
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013)
- TLS_DHE_RSA_WITH_AES_128_CBC_SHA (0x33)
- Because no forward secrecy is offered (some also use CBC and/or SHA1)
- TLS_RSA_WITH_AES_256_GCM_SHA384 (0x9d)
- TLS_RSA_WITH_AES_128_GCM_SHA256 (0x9c)
- TLS_RSA_WITH_AES_256_CBC_SHA256 (0x3d)
- TLS_RSA_WITH_AES_256_CBC_SHA (0x35)
- TLS_RSA_WITH_AES_128_CBC_SHA256 (0x3c)
- TLS_RSA_WITH_AES_128_CBC_SHA (0x2f)
Regarding when "CBC is used"
According to the security team: "CBC being offered is ok as long as its a strong cipher. That is no 3DES ciphers offered". All offered ciphers are strong is this regard (e.g. no 3DES is offered).
Conclusion: Leave it as it is
Regarding "SHA1 is used"
This is considered OK because SHA1 is used as HMAC-SHA1 which is not broken (unlike pure SHA1). All offered ciphers are strong in this regard.
Security team: "While SHA1 is broken, HMAC-SHA1 is not broken. Assuming that the HMAC key is not known to the attacker, HMAC-SHA1 is not susceptible to the same collision attacks that SHA1 is. If the attacker has the HMAC key, he has broken HMAC itself, no matter if it is HMAC-SHA1 or HMAC-SHA2."
Conclusion: Leave it as it is
Regarding "no forward secrecy is offered"
The overall SSL Labs rating does not change if the non-forward secrecy ciphers are removed.
SSLCipherSuite ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:!aNULL:!MD5:!DSS
Less capable clients will lose support if the non-forward secrecy ciphers are removed. Clients that support forward secrecy will prefer the forward secrecy ciphers anyway.
Conclusion: Leave it as is, as it has no impact on clients that support forward secrecy but widens the support for less capable clients
As you can see if you remove the CBC ciphers from the list, you are limiting the client pool that can connect to your WAF instance. You must also ensure that the default WAF settings for the TLS version has not been altered from TLS1.0. Doing so will override the SSL settings configured in the file listed below.
- If you would like to remove various ciphers, the file to edit is located here:
/usr/apache/conf/httpd.conf - You need to put the system into read/write mode:
mount -no remount, rw / - Then edit the above file with VI and locate the following line: Include /cfs/waf/reverseproxy.conf:
The above line is normally located at the end of the file.
- Add your own SSLProtocol and SSLCipherSuite options here. Make sure that you follow the syntax specified by Apache and OpenSSL. For more information, you can refer to the Apache documentation at mod_ssl - Apache HTTP Server Version 2.4 and mod_ssl - Apache HTTP Server Version 2.4
-
Save the file.
-
Put the filesystem back to read-only mode:
mount -no remount, ro / -
Restart WAF for the changes to take effect:
service -ds nosync waf:restart
Note: that when WAF is set to use TLS1.2, 3DES ciphers aren’t offered to the client.
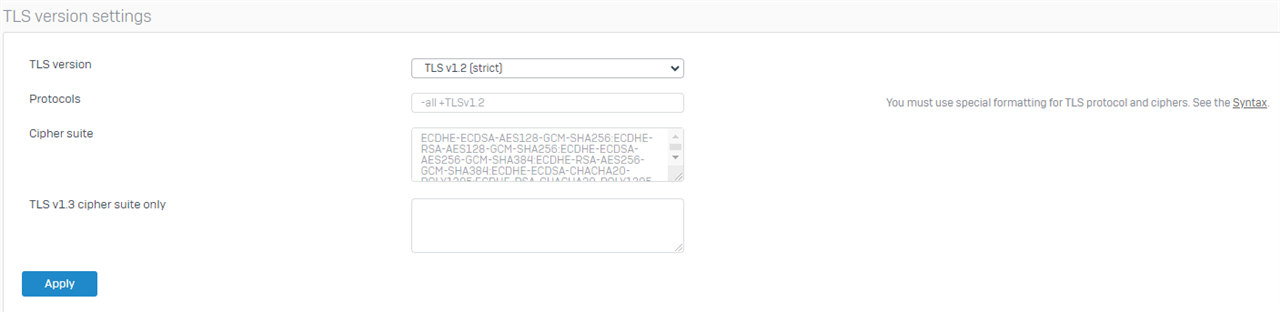
v20
From Version 20, you can change the ciphers through the UI. The TLS version has been extended to a stricter TLS 1.2 and a TLS 1.3 specific cipher set. An additional custom option that allows you to configure whatever protocol version and cipher you want has also been added. This means you no longer need to manually edit any files.
Protect > Web Server > General Settings > TLS Version settings
Horizontal Lines, and v20 newest information
[edited by: emmosophos at 6:17 PM (GMT -8) on 17 Nov 2023]
