A new version of the Sophos Web Appliance software is being rolled out starting this week. Version 4.3.4 combines a number of fixes for reported bugs, including a potential vulnerability reported to us by Christian Demko of MWR InfoSecurity. Thanks to Christian for notifying us of this issue.
A list of issues addressed in this version can be found in the release notes.
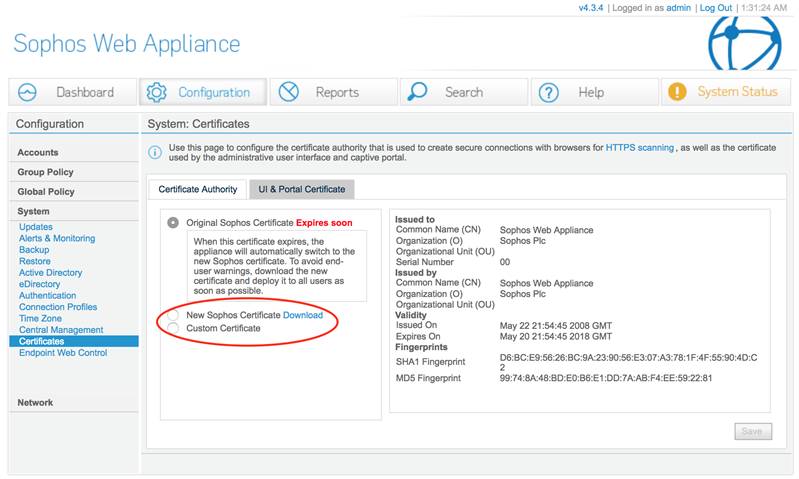
It also includes an update to the built-in Certificate Authority (CA) used for HTTPS decryption, as the current certificate is due to expire in May 2018.
To avoid end-user disruption, you will need to ensure that all end-user devices trust the new certificate before you make the switch to using it on your Web Appliance. We have provided a link to download the new certificate from the SWA Admin UI (Configuration > System > Certificates), so you can deploy it to endpoints via Active Directory, email or some other method.
When the end-user devices are ready, you can activate the new certificate by clicking on the "New Sophos Certificate" radio button on that page. Once activated, you can't switch back to the old certificate. Your Web Appliance will automatically switch to the new CA on May 20, 2018.
Improve security with a custom CA
Sophos Web Appliance provides with a built-in CA as a convenience. This CA is common to all SWA installations. When end-user devices use this CA as a trusted authority, they will trust any certificate signed with this authority by any Web Appliance.
You can improve the security of the HTTPS decryption process by using a custom CA instead of the built-in one. With a custom CA your end-user devices will only trust certificates created on your Web Appliances.
Because you need to roll out a new CA to end-user devices anyway, now might be a good time to make the switch to a custom CA.
If you have access to a system with OpenSSL (most Linux distributions, Mac OSX or installable Windows environments like Cygwin have this) it's a pretty straightforward process. We have published a knowledgeable article describing the process.