Hi,
In my setup i run a Sophos UTM v9.413-3 and i have two AP's connected to it, one AP55C and one AP30. This was working just fine for a long time, but recently i noticed my wifi connection in was getting worse, so i looked at the logging and i noticed that since december 2016 i started to get alot of failed connection attempts.
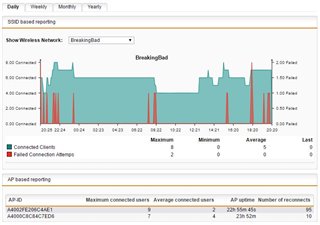
this is how it daily looks now.
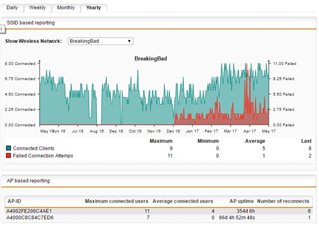
This is the yearly one, where you can see it started out of the blue in december.
I do see these log messages, but im not sure if they have anything to do with it.
This thread was automatically locked due to age.