Hi,
We want to drop/reject connection from some IP address, these IPs shouldnt have access to anything not from WAF rules or from DNAT rules
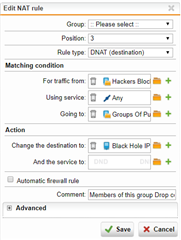
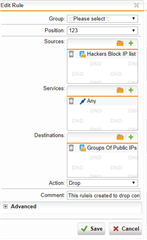
from what I understand we should create a DNAT rule and point it to a machine that is not exsit and group the IPs that we want to block them to a group and add them as the source of new DNAT.
But this will still process the connections that comes to the utm. we want to drop the connection or reject connection from these IPs.
can we create the DNAT rule and put it on the possition 1 and also instead of creating the firewall rule automatically for the DNAT, create a firewall rule manually and use the drop or reject connection from there?
Thanks
This thread was automatically locked due to age.