I am trying to host a website through Sophos UTM and setting up a DMZ
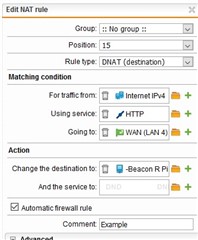
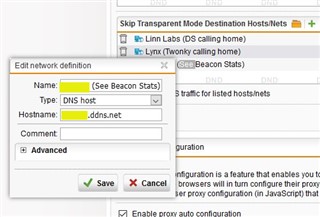
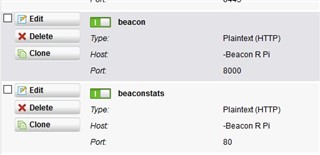
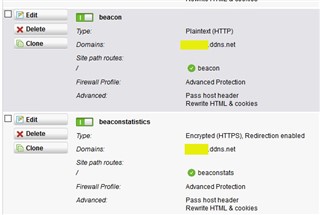
I configured the website in IIS and configured the webserver in Sophos UTM
did the port forwarding in the router tested it on the server and it worked
when I test the website I get not found 404 error this is with a NOIP hostname
when I test it with the public IP address I get forbidden error
no problem with the IIS configuration I tested it without going through Sophos UTM and it works
this is the guide I followed in configuring the webserver in Sophos UTM
This thread was automatically locked due to age.