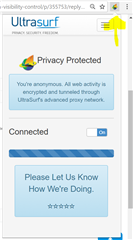
Hi Sophos Community
Good Day,
Is there any way to block ultrasurf addons/extensions in google chrome browser?
Or is there anyway that the users may have not access to add utilities on Google chrome - browser?
Scenario.
Web protection > transparent mode > decrypt and scan > anonimyzers and utilities
Filter action
* Block anonymizers and utilities
* Block jobsearch
But after turning on of ultrasurf addons in my browser.. you can now browse anything you want
Thank you
PS.
I already been blocked these urls after searching in sophos community but sadly no luck, ultrasurf still running
https://[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}/
http://[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}/
https?://[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}/
This thread was automatically locked due to age.