Hello,
i want to configure a excepting a certain destination on the web filter. but i can't complete this configuration.
(Web filtering is in transparent. )
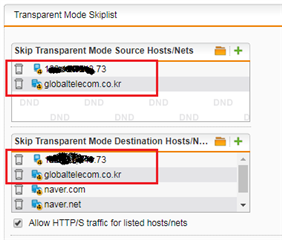
So i tried to add the destination url on the "Skip transparent mode destination host/nets" following KB 120839.
community.sophos.com/.../120839
but exception is not working well.
For example, i want to except the google.com on the web filtering.
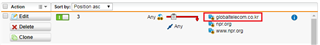
So i add the www.google.com to the "Skip transparent mode destination host/nets".
but when i access the google.com, http.log is generated regarding google.com. (action="pass")
It would be much appreciated, if anyone helps me to configure an exception on web filter.
This thread was automatically locked due to age.