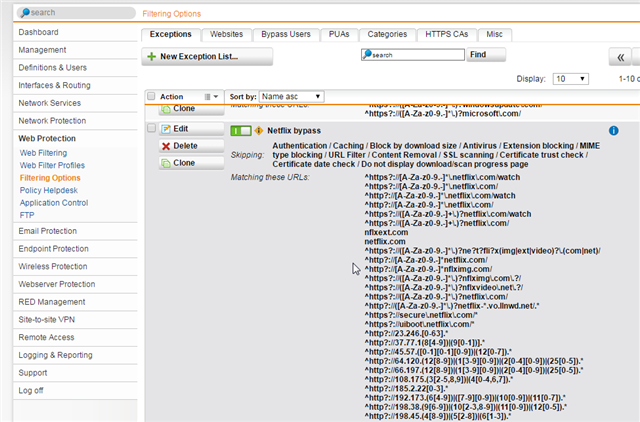
I know other admins have been looking for a solution to allow streaming Netflix content without whitelisting a device. Another user posted a solution in the XG Group that worked for me with UTM9
https://community.sophos.com/products/xg-firewall/f/129/t/74689
The same logic could probably be used for other streaming services as well.
This thread was automatically locked due to age.