Hi All,
Happy Monday. I'm on an SG230 with 9.601-5.
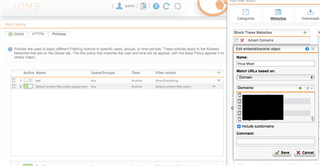
I'm at a loss why web filtering is not working. I have a number of sites I want to block, and put them into a group I call "Virus Moat" in the Default Content Filter action. But I can still navigate to the site from any computer on my network. The only way I can block them it through a firewall rule. I don't understand what I'm missing.
Thanks,
Jeff
This thread was automatically locked due to age.