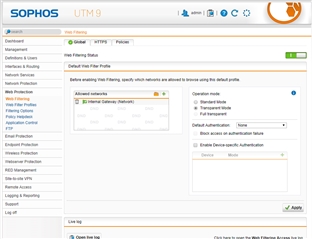
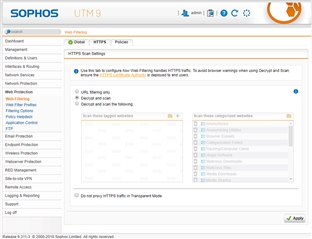
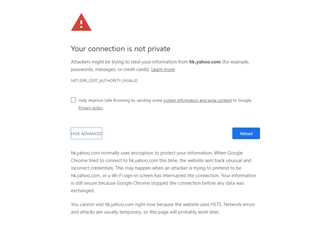
I am very tired because UTM 9 can't block the link successfully.
Following is the link
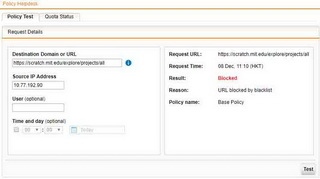
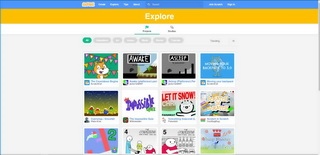
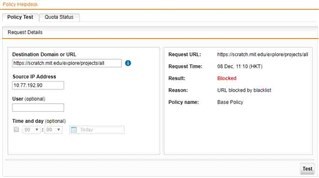
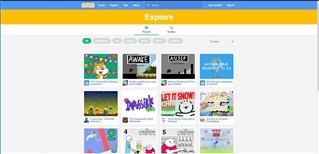
" https://scratch.mit.edu/explore/projects/all "
I tested follow Regular Expression :
" https://scratch.mit.edu/explore/projects/[all] "
" https://scratch.mit.edu/explore/projects/[a-zA-Z0-9] "
When I use policy test, it shows blocked. However I try the user computers (total 10 different computers), it can be passed.
Include the last "Lego" Game link, this is the second link that can't be blocked.
Please help!
This thread was automatically locked due to age.