Hi, I'm having some trouble getting a proxy configuration to work correctly.
Actually a customer is using transparent proxy for his internal network - everything is working fine. Now he has a new VLAN where some guest workers are separated. He wants to deny all web traffic for this new VLAN except "windows updates".
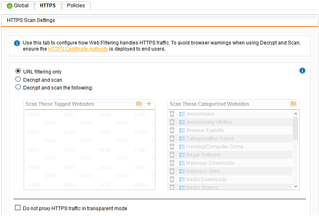
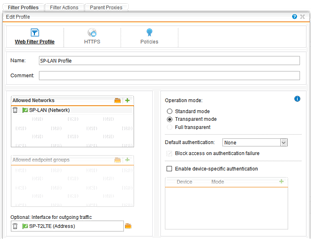
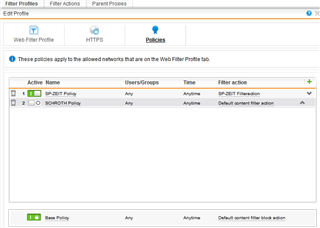
I changed the "Default Web Filter Profile" to accept connections from both networks (UTM is gateway for both). HTTPS Scan Settings is set to "URL filtering only" and no policy is active for that profile. "Base Policy" is working with "Default content filter block action".
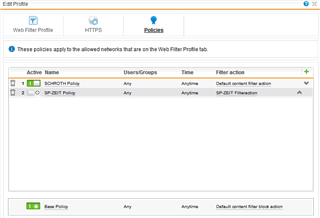
Then I created a new Policy for the internal network. "Allowed network" is only the internal network, HTTPS and mode settings set as in default profile, only the policy for the internal network with it's own filter action ("Allow all content, except...") is active. Surfing is working as before for the internal network.
Now I sat up nearly the same for the VLAN. "Allowed network" is only the VLAN network, HTTPS and mode settings as in default profile, an own policy with an own filter action (copy of "Default content filter block action", therefore "Block all content, except...") to disallow anything at first and to be able to allow some pages without changing the default filter action.
I did not use authentication anywhere and I did not use https-decryption, only "URL filter".
Now to my problems:
- if I call http://www.sophos.com from the VLAN the "content blocked (blocked category)" page is shown, okay so far but with a small failure: a "unblock page" button is also shown. I could live with that but I don't understand why it is shown.
- if I call https://www.sophos.com something weird is happening. The proxy behaves like if I have https-decryption active. First that is shown is a certificate error containing the UTM's proxy CA certificate. If I proceed the error the content blocked page is shown, too but the layout is completely destroyed.

Any hints where I have misconfigured something would be nice. Again, authentication and https-decryption is not active in any of the profiles, so why does the proxy behave like it is active?
This thread was automatically locked due to age.