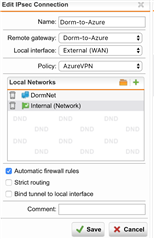
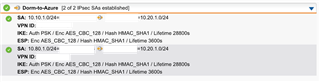
I am hoping somebody can help with this issue. I have an Azure Site to Site VPN that has connected fine. However when I try to ping or use RDP on the remote network. It doesn't work. I am behind a firewall at my college that allows no ports through. Does UDP/500 need to be open. I am getting errors like "sending encrypted notification INVALID_PAYLOAD_TYPE to xx:500" and "message ignored because it contains an unexpected payload type (ISAKMP_NEXT_HASH)". I have attached my configuration and a snippet of a log file from my UTM.
{\rtf1\ansi\ansicpg1252\cocoartf1671\cocoasubrtf100
{\fonttbl\f0\fmodern\fcharset0 Courier;}
{\colortbl;\red255\green255\blue255;\red0\green0\blue0;\red224\green223\blue220;}
{\*\expandedcolortbl;;\cssrgb\c0\c0\c0;\cssrgb\c90196\c89804\c89020;}
\margl1440\margr1440\vieww28600\viewh15460\viewkind0
\deftab720
\pard\pardeftab720\sl280\partightenfactor0
\f0\fs24 \cf2 \cb3 \expnd0\expndtw0\kerning0
\outl0\strokewidth0 \strokec2 2018:12:12-23:10:47 krohtofw pluto[26798]: "S_Dorm-to-Azure" #250: IKE message has the Commit Flag set but Pluto doesn't implement this feature; ignoring flag\
2018:12:12-23:10:47 krohtofw pluto[26798]: id="2203" severity="info" sys="SecureNet" sub="vpn" event="Site-to-site VPN up" variant="ipsec" connection="Dorm-to-Azure" address=\'93xx\'94 local_net="10.80.1.0/24" remote_net="10.20.1.0/24"\
2018:12:12-23:10:47 krohtofw pluto[26798]: "S_Dorm-to-Azure" #250: sent QI2, IPsec SA established \{ESP=>0x8f86e1c8 <0x1faa1fb4\}\
2018:12:12-23:10:47 krohtofw pluto[26798]: packet from xx:500: Informational Exchange is for an unknown (expired?) SA\
2018:12:12-23:10:47 krohtofw pluto[26798]: "S_Dorm-to-Azure" #249: IKE message has the Commit Flag set but Pluto doesn't implement this feature; ignoring flag\
2018:12:12-23:10:47 krohtofw pluto[26798]: "S_Dorm-to-Azure" #249: message ignored because it contains an unexpected payload type (ISAKMP_NEXT_HASH)\
2018:12:12-23:10:47 krohtofw pluto[26798]: "S_Dorm-to-Azure" #249: sending encrypted notification INVALID_PAYLOAD_TYPE to xx:500\
2018:12:12-23:10:47 krohtofw pluto[26798]: "S_Dorm-to-Azure" #250: IKE message has the Commit Flag set but Pluto doesn't implement this feature; ignoring flag\
2018:12:12-23:10:47 krohtofw pluto[26798]: "S_Dorm-to-Azure" #250: message ignored because it contains an unexpected payload type (ISAKMP_NEXT_HASH)\
2018:12:12-23:10:47 krohtofw pluto[26798]: "S_Dorm-to-Azure" #250: sending encrypted notification INVALID_PAYLOAD_TYPE to xx:500\
}
This thread was automatically locked due to age.