Hello all,
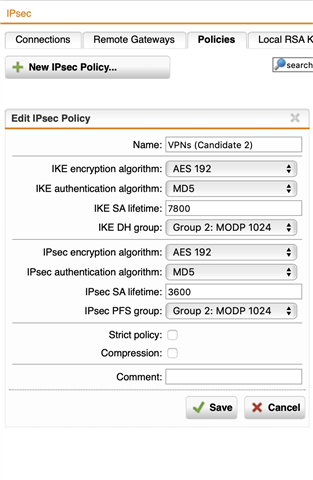
Long time Sophos UTM users here. We have three offices and a HP ProLiant G9 in each office running Sophos UTM in Chicago, Seattle and Los Angeles. We're running Teradici PCoIP that requires the best throughput and lowest latency possible between the sites. Teradici uses both TCP and UCP for it's PCoIP protocol, so I'm not sure if running over a TCP IPSec S2S vpn is ideal. We're around 44-46ms and latency is the highest priority, looking to optimize our policies a bit better as I know they are out of whack! I've read something about AES 128 GCM using hardware acceleration on intel processors, looking for tweaks like that to speed up our IPSec connections between sites. I've included a screen grab of our VPN policy.
Any help would be much appreciated!!
This thread was automatically locked due to age.