Hi All
I am trying to get a better understanding of the differences between the 2. I am using UTM 9 on SG125
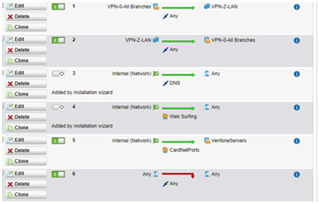
I have multiple IPSEC sites (Grouped as VPN-0-All Branches) all connecting to Head Office (VPN-Z-LAN).
So I do not enable automatic firewall rules but set to manual rules as follows Key being 1&2 (Allow between Branch & HO Any + HO & Branch Any)
My application (using single port for connection) connects fine under above but I cannot access anything else such as web access to remote router or remote desktop via IP address
If I enable rule 4 (Web Surfing) I can access remote router but still cannot remote desktop to a machine at branch using IP address i.e.
However if I let UTM create an auto rule all works fine (even if I have all others disabled) e.g. In this example have allowed creation of auto firewall rule between Branch B and Z Any
In this case all works fine. So what's the difference? [:^)]
Is it the case the in manually created rule "Any" is not the same thing as "Any" on the auto created rule or something else?
Any insight would be appreciated
This thread was automatically locked due to age.