Hi,
i have multiple site-to-site ipsec vpns between an ASG220 and Bintec-Routers.
All connections work fine but the log is filled with messages like these:
2018:10:21-15:16:48 firewall_name pluto[6401]: "S_VPN_Name"[1] 126.74.24.27:48964 #3558946: max number of retransmissions (2) reached STATE_MAIN_I3. Possible authentication failure: no acceptable response to our first encrypted message
2018:10:21-15:16:48 firewall_name pluto[6401]: "S_VPN_Name"[1] 126.74.24.27:48964 #3558946: starting keying attempt 973 of an unlimited number
2018:10:21-15:16:48 firewall_name pluto[6401]: "S_VPN_Name"[1] 126.74.24.27:48964 #3558965: initiating Main Mode to replace #3558946
2018:10:21-15:16:48 firewall_name pluto[6401]: "S_VPN_Name"[1] 126.74.24.27:48964 #3558965: ignoring Vendor ID payload [some id]
2018:10:21-15:16:48 firewall_name pluto[6401]: "S_VPN_Name"[1] 126.74.24.27:48964 #3558965: ignoring Vendor ID payload [more id]
2018:10:21-15:16:48 firewall_name pluto[6401]: "S_VPN_Name"[1] 126.74.24.27:48964 #3558965: ignoring Vendor ID payload [jet another id]
2018:10:21-15:16:48 firewall_name pluto[6401]: "S_VPN_Name"[1] 126.74.24.27:48964 #3558965: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03]
2018:10:21-15:16:48 firewall_name pluto[6401]: "S_VPN_Name"[1] 126.74.24.27:48964 #3558965: ignoring Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n]
2018:10:21-15:16:48 firewall_name pluto[6401]: "S_VPN_Name"[1] 126.74.24.27:48964 #3558965: ignoring Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02]
2018:10:21-15:16:48 firewall_name pluto[6401]: "S_VPN_Name"[1] 126.74.24.27:48964 #3558965: ignoring Vendor ID payload [draft-ietf-ipsec-nat-t-ike-00]
2018:10:21-15:16:48 firewall_name pluto[6401]: "S_VPN_Name"[1] 126.74.24.27:48964 #3558965: received Vendor ID payload [XAUTH]
2018:10:21-15:16:48 firewall_name pluto[6401]: "S_VPN_Name"[1] 126.74.24.27:48964 #3558965: received Vendor ID payload [Dead Peer Detection]
2018:10:21-15:16:48 firewall_name pluto[6401]: "S_VPN_Name"[1] 126.74.24.27:48964 #3558965: enabling possible NAT-traversal with method RFC 3947
If i reset the connection the log is silent for several hours.
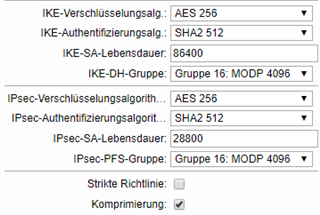
Settings on the Sophos:
Answer only.
Remote-Network: 10.10.2.0/24
Local-Network: 10.10.0.0/16
PMTU on, automatic firewall-rules on
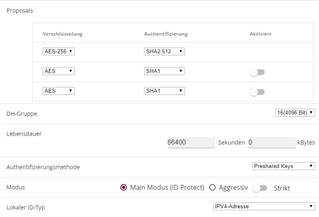
Settings on Bintec:
IKEv1
VPN-ID 10.10.2.1
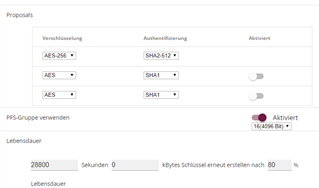
Phase2:
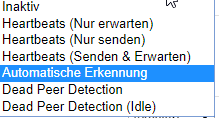
Also:
Nat-t on
Availability-check: auto
PMTU on
Hope you can give me some insight to what the logs are trying to tell me.
Greetings
This thread was automatically locked due to age.