Hi,
The main purpose of this question is to filter and find the most recent and working solution for implementing a virtual network gateway between Azure ans Sophos UTM, because i have been following multiples guides with similar configuration and yet, i don't have any success so far.
Guides followed:
- https://techstat.net/azure-sophos-utm-site-site-vpn-ipsec-settings-ikev1-policy-based/
- https://community.sophos.com/kb/en-us/126995
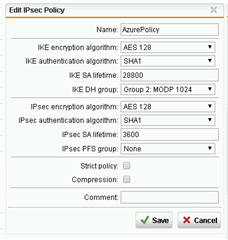
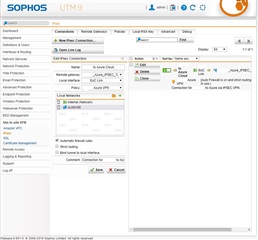
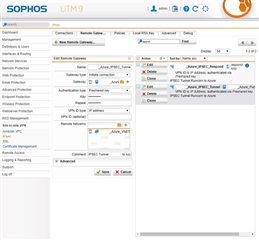
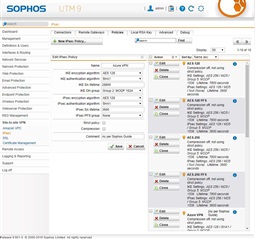
Currently, without much experience on Sophos UTM and following the first and second guide, i was able to have a connection working between our networks but the connection is always dropping, so my main question would be how could i find a more recent and working guide for setting up one or multiples gateways between azure and sophos UTM ?
Thanks in advance.
This thread was automatically locked due to age.