Hello all,
Hope everyone is staying safe and healthy in these times. I've been tasked with deploying 2 RED50s, to 2 different locations. Having only deployed a RED15w to another remote office it took me 2 days and some help onsite (site had static IP and was configured for a different subnet). I'm going to have to do the same thing for another RED50 this time so I think I can handle that on, provided my onsite help can handle hotspotting (for the DHCP portion of the setup). :)
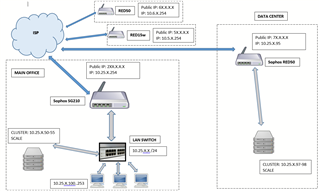
However, the second RED50 is what will have me perplexed. It is the only one of the bunch that I actually have on hand before deployment and it is also the one that needs to be a part of the same subnet. This RED50 is going into a data center to handle our offsite cluster (backup and disaster recovery). I have our (soon to be) offsite cluster configured and working perfectly in our present LAN setup.
Local Sophos UTM is SG210 on 9.702 fw.
The questions I have for this deployment: ( networking is NOT my forte :) )
1 - Can I pre-configure the RED50 locally in office, register it and then change the IP / gateway to static, power it down and move it to the data center
2 - How can I configure the RED50 and the SG so that the RED50 acts as an extension of the current LAN? (LAN is 10.x.x.x/24, SG is the DHCP server and dishes out IPs from .100 up) I want the RED50 to have 10.x.x.95 and the cluster already has .97 and .98 assigned to it.
3 - Any suggestions on how to make my life easier on configuring future REDs to remote sites with static IPs?
This thread was automatically locked due to age.