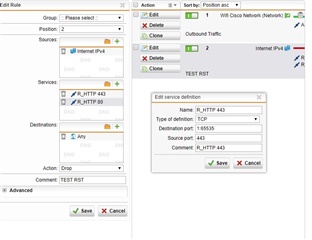
Hi, I have set up a UTM all working fine outgoing for internet but started getting lots of [RST] connection which are inbound on ports 80 & 443. I understand this to be normal and are dropped connections. My question is how can I create a rule to stop them logging as they are just flooding the log !!!!
We are using a SG135 on firmware 9.504-1
Any advice??
| 15:56:18 | Default DROP | TCP |
|
→ |
|
|
| 15:56:22 | Default DROP | TCP |
|
→ |
|
|
This thread was automatically locked due to age.