I can't access the WebAdmin despite being connected via VPN (SSL).
Here's the basic configuration:
The UTM has a publicly accessible hostname (with matching certificate) - COMPANY.COM -> our public IP
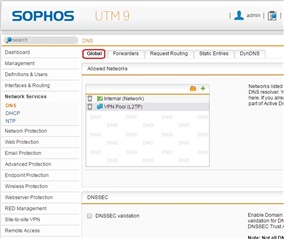
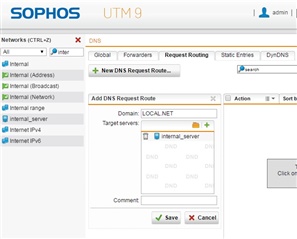
On our internal DNS it also has a local DNS entry - UTM.LOCAL.NET -> UTM local IP
The WebAdmin has been configured to allow all connected from our internal network, as well as the IP pools for SSL.
After I connect via VPN (SSL), I can't connect via the COMPANY.COM address, but I CAN connect using the UTM.LOCAL.NET address. That said, any machines which are physically in our LAN can indeed connect to the WebAdmin using the public DNS name.
When checking the logs, it logs a blocked WebAdmin access attempt coming not from the assigned VPN IP, but from my home IP. On one hand, this is understandable, but on the other... how do I make this work?
My only idea thus far is to add a local DNS entry overriding the COMPANY.COM public DNS, so it points to the internal LAN IP of our UTM, rather than the public IP... but there's a minor issue with that (unrelated to this question) and feels like a workaround rather than an actual solution to the problem.
So... what could I do?
This thread was automatically locked due to age.