Sorry for my English.
I have a problem on my Utm 9.502-4 Pattern 130909 Home Edition.
The problem started just after installation before any configuration.
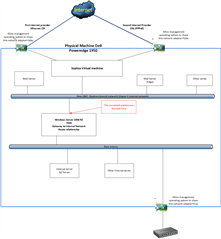
I have a network composed by a DMZ (Sophos internal network) and my internal network.
All computer are virtual machines.
The firewall between Internet and DMZ is Sophos
The firewall between DMZ and internal network is Microsoft TMG
The problem is: Tmg Firewall denied connection to packet from external IP that should have blocked by Sophos.
If I disable the internet connection the packets dosn't arrive.
On Sophos there is a static route to internal network.
I have tested another IP in DMZ and it doesn't receive any unwanted packet.
Only the gateway to internal network seems to receive unwanted packets.
Below:
- A list of some IP sending unwanted packet.
I have tested, someone has not bad reputation.
2.17.205.2
2.19.70.112
23.21.45.59
43.137.167.137
52.222.171.187
54.171.245.137
54.192.27.68
64.233.167.155
74.125.206.157
89.163.159.115
93.184.221.200
130.211.5.178
178.250.0.71
185.33.223.202
192.229.223.25
199.96.57.6
213.215.153.102
216.52.1.12
216.58.205.33
216.58.205.34
216.58.205.130
216.58.205.162
216.58.205.166
217.12.15.83 - The list from TMG showing ports.
The ports have always an high number.
I have tried:
Sorry for my English.
I have a problem on my Utm 9.502-4 Pattern 130909 Home Edition.
The problem started just after installation before any configuration.
I have a network composed by a DMZ (Sophos internal network) and my internal network.
All computer are virtual machines.
The firewall between Internet and DMZ is Sophos
The firewall between DMZ and internal network is Microsoft TMG
The problem is: Tmg Firewall denied connection to packet from external IP that should have blocked by Sophos.
If I disable the internet connection the packets dosn't arrive.
On Sophos there is a static route to internal network.
I have tested another IP in DMZ and it doesn't receive any unwanted packet.
Only the gateway to internal network seems to receive unwanted packets.
Below:
- A list of some IP sending unwanted packet.
I have tested, someone has not bad reputation.
2.17.205.2
2.19.70.112
23.21.45.59
43.137.167.137
52.222.171.187
54.171.245.137
54.192.27.68
64.233.167.155
74.125.206.157
89.163.159.115
93.184.221.200
130.211.5.178
178.250.0.71
185.33.223.202
192.229.223.25
199.96.57.6
213.215.153.102
216.52.1.12
216.58.205.33
216.58.205.34
216.58.205.130
216.58.205.162
216.58.205.166
217.12.15.83 - The list from TMG showing ports.
The ports have always an high number.
I have tried:
Notwithstanding my attempts the packets continue to arrive and are dropped by TMG.
Any Idea ?
This thread was automatically locked due to age.