Hi all:
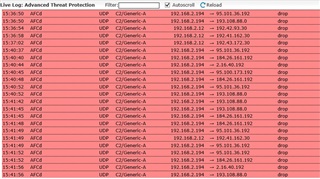
I check our company Sophos UTM9 firewall, Advanced Threat Protection part, this have threat name "C2/Generic-A" events for AD/DNS Server as follow:
I use the sophos endpoint, malwarebytes & superantispyware to run full scan, but can't find any aviurs, Please help me to fix this problem, thanks a lot!
PS: 192.168.2.194 is primary AD & DNS Server, 192.168.2.12 is secondary AD & DNS Server.
|
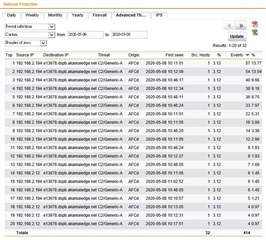
Advanced Threat Protection
|
Total Events: 32
| User/Host | Threat Name | Destination | Events | Origin | ||
| 1 | 192.168.2.194 | C2/Generic-A | 104.31.83.243 | 5 | AFCd | |
| 2 | 192.168.2.194 | C2/Generic-A | 104.31.83.243 | 5 | AFCd | |
| 3 | 192.168.2.12 | C2/Generic-A | mi.kenal-cn.com | 1 | AFCd | |
| 4 | 192.168.2.12 | C2/Generic-A | mi.kenal-cn.com | 1 | AFCd | |
| 5 | 192.168.2.194 | C2/Generic-A | mi.kenal-cn.com | 2 | AFCd | |
| 6 | 192.168.2.194 | C2/Generic-A | mi.kenal-cn.com | 2 | AFCd | |
| 7 | 192.168.2.12 | C2/Generic-A | mi.kenal-cn.com | 1 | AFCd | |
| 8 | 192.168.2.194 | C2/Generic-A | mi.kenal-cn.com | 1 | AFCd | |
| 9 | 192.168.2.12 | C2/Generic-A | mi.kenal-cn.com | 1 | AFCd | |
| 10 | 192.168.2.194 | C2/Generic-A | mi.kenal-cn.com | 2 | AFCd |
This thread was automatically locked due to age.