Hello,
we have two Sophos UTM HA-Clusters in our network.
The first Cluster (SG330) is used as external gateway. There is the web proxy module enabled (Port: 8080)
The second cluster (SG450) is used as internal gateway for routing purposes and firewalling for our seperated client networks (VLANs / Subnets).
Now i can see drops in the internal gateway of requests from web proxy (external gateway) back to clients behind the internal gateway.
Example:
Success --> Outgoing traffic: Client #1 - IP: 192.168.178.5 - Gateway = internal gateway (10.46.0.70) ---> Proxy connection to external gateway (10.46.0.34:8080) ----> WAN
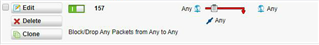
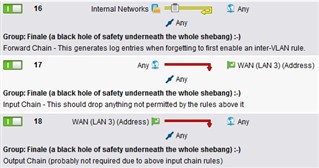
Block in internal gateway --> Incoming traffic: WAN ----> external gateway (10.46.0.34:8080) ---> back to client behind internal gateway (10.46.0.70) ---> 192.168.178.5:60555
There are many connections going to the clients back from the proxy ip address to the clients ip address with dynamic (high) ports.
is that behaviour normal? the users don't report any issues and no performance problems.
Should i allow the traffic from: 10.46.0:34:8080 back to the client networks behind the internal firewall gateway?
Thanks so far.
This thread was automatically locked due to age.