We are having an issue with our UTM 9.605-1 device. We have user reports of poor connection quality when using video conference and web-browser based phone calling services (Twilio).
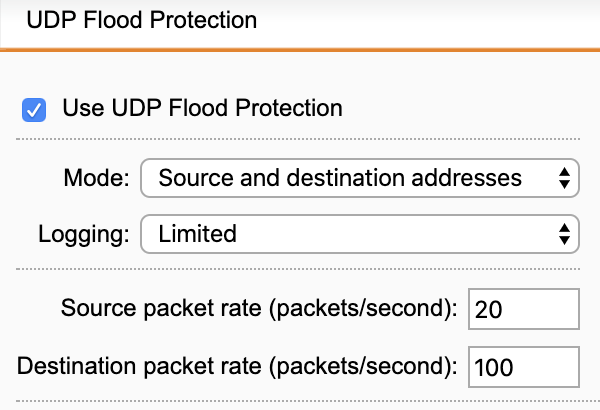
We have the IPS enabled globally, and we have UDP flood protection enabled with settings:
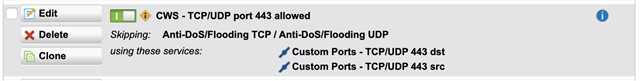
We were experiencing some logging of "name="UDP flood detected" action="UDP flood" fwrule="60013" in the logfile, so I made the decision to enter an exception for inbound and outbound traffic using these various TCP and UDP ports:
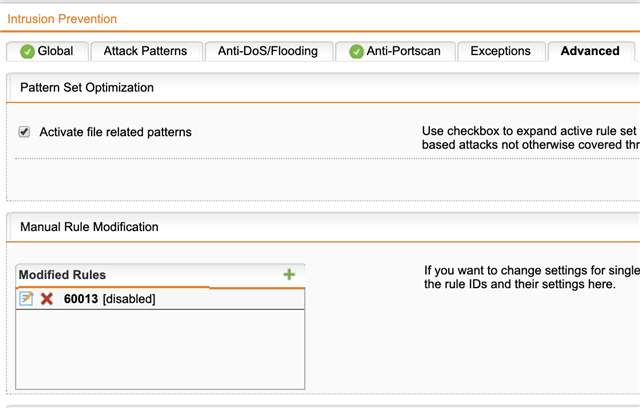
But the UDP flood detected messages were still appearing in the log file. So then I attempted to disable the offending UDP flooding rule, specifically: fwrule="60013" as follows:
But even after that I am still seeing UDP flood detected messages in the log file regarding that same fwrule:
2020:02:06-10:16:13 utm-2 ulogd[17598]: id="2105" severity="info" sys="SecureNet" sub="ips" name="UDP flood detected" action="UDP flood" fwrule="60013" initf="eth4" srcmac="64:64:9b:56:44:00" dstmac="00:1a:8c:f0:6e:e4" srcip="173.194.162.140" dstip="209.131.229.254" proto="17" length="1378" tos="0x00" prec="0x00" ttl="61" srcport="443" dstport="49277"
2020:02:06-10:16:13 utm-2 ulogd[17598]: id="2105" severity="info" sys="SecureNet" sub="ips" name="UDP flood detected" action="UDP flood" fwrule="60013" initf="eth4" srcmac="64:64:9b:56:44:00" dstmac="00:1a:8c:f0:6e:e4" srcip="173.194.162.140" dstip="209.131.229.254" proto="17" length="1378" tos="0x00" prec="0x00" ttl="61" srcport="443" dstport="49277"
2020:02:06-10:16:14 utm-2 ulogd[17598]: id="2105" severity="info" sys="SecureNet" sub="ips" name="UDP flood detected" action="UDP flood" fwrule="60013" initf="eth4" srcmac="64:64:9b:56:44:00" dstmac="00:1a:8c:f0:6e:e4" srcip="173.194.162.140" dstip="209.131.229.254" proto="17" length="1378" tos="0x00" prec="0x00" ttl="61" srcport="443" dstport="49277"
in the above example, 209.131.229.254="External (WAN) - Jaguar Comm (Address)" so it should be in my exception list AND the rule 60013 should be disabled anyway. It appears as though the exceptions listed, as well as completely disabling the rule in the advanced section have no effect.
Can someone shed some light on my situation? Thanks.
This thread was automatically locked due to age.