Hi to all,
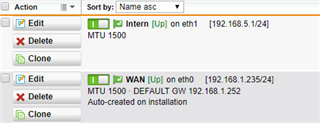
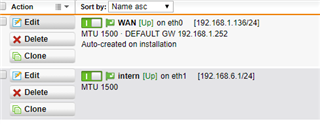
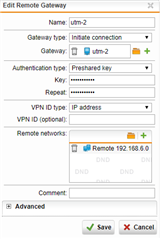
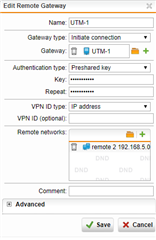
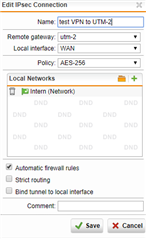
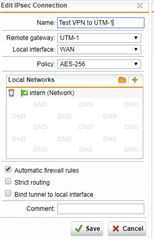
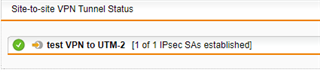
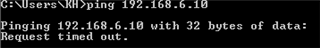
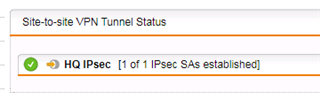
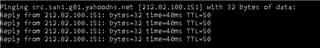
I have one UTM 9 at HQ site and one UTM 9 at branch site with IPSec Active tunnel between them.
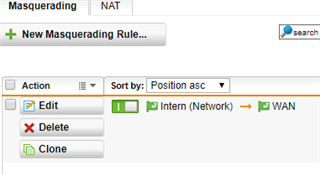
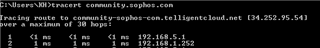
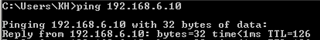
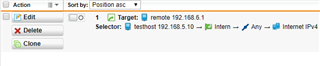
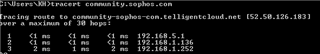
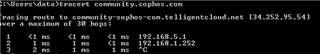
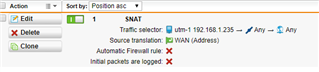
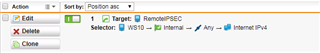
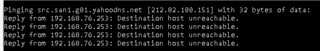
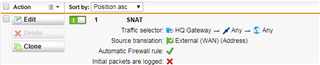
I would like, only for some specific hosts in HQ site, to present themselves on Internet using Branch site WAN IP address instead of HQ wan IP.
It is possible with some SNAT / routing rule? What would be the best way to address it?
thank you all
This thread was automatically locked due to age.