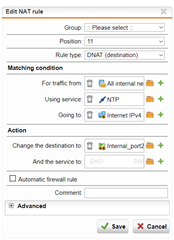
I'm migrating a customer over to the XG firewall and they're not sure what devices are statically assigned the UTM as their NTP server.
I know I can do tcpdump dst port 123, but that will show all traffic for NTP (not just NTP traffic straight to the firewall).
I've tried tcpdump host 10.110.10.1 port ntp, but I get invalid syntax.
This thread was automatically locked due to age.