Hi,
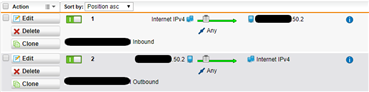
I'm seeing some strange behaviour for NAT of DMZ traffic out to the Internet. Traffic is allowed both outbound and inbound;
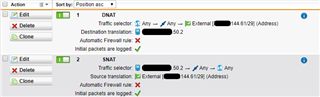
There is a masquerade rule in place for the internal network;
Source: Internal_Network (10.0/8 and 192.168.0/16)
Interface: External
Use Address: <<Primary Address >> (x.x.144.58/29)
There are also specific NAT rules in place for the DMZ network above (10.10.50.0/24);
However, a tcpdump shows that HTTPS traffic out to the internet is sitting behind the Primary Address (x.x.144.58) and not the SNAT address (x.x.144.61)
<M> utm01:/root # tcpdump -v -nni eth1 host 35.156.229.155 and tcp
tcpdump: listening on eth1, link-type EN10MB (Ethernet), capture size 65535 bytes
11:20:33.243219 IP (tos 0x0, ttl 64, id 62526, offset 0, flags [DF], proto TCP (6), length 60)
x.x.144.58.39422 > 35.156.229.155.443: Flags [S ], cksum 0x64d1 (incorrect -> 0x256d), seq 2987452050, win 29200, options [mss 1460,sackOK,TS val 81203884 ecr 0,nop,wscale 7], length 0
11:20:33.559246 IP (tos 0x0, ttl 39, id 0, offset 0, flags [DF], proto TCP (6), length 60)
35.156.229.155.443 > x.x.144.58.39422: Flags [S.], cksum 0x2142 (correct), seq 1583871935, ack 2987452051, win 28960, options [mss 1460,sackOK,TS val 713589850 ecr 81203884,nop,wscale 7], length 0
Any ideas what might be affecting that? I'm checking on the routing to see if there is anything that needs to be updated there.
Thanks,
Colin
This thread was automatically locked due to age.