Hi
We have a Utm and at the moment we do not have or need a Dmz
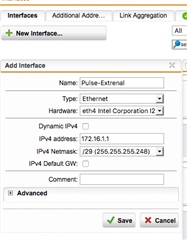
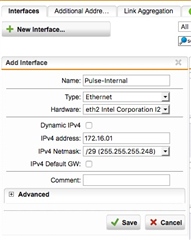
We have just bought a pulse secure appliance that has two network ports internal and external.
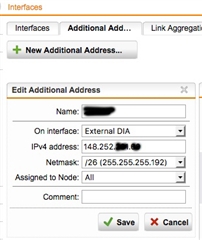
I’m trying to decide the best way to set it up. If I create a new interface with a new IP address range and plug the wan connection from the pulse box not that. I can then nat an IP address to that box. I can block all the ports that I don’t need. If I then put the lan cable from the pulse secure box into our core switch the pulse secure box will have access to all internal systems.
However, I’m not sure what benefit this gives me over just setting up NAT straight to the pulse secure box that’s on the lan.
Can anyone think of a better way to do it?
This thread was automatically locked due to age.