I'm trying to block devices on the internal network from accessing other devices on the internal network.
Simple, right? Of course not....
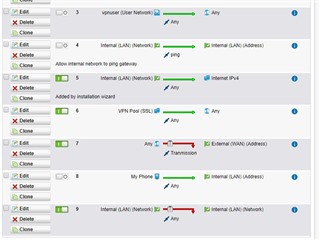
I create a firewall rule Internal (Network)->ANY->Internal (Network)->Block
even Internal (Network)->File Transfer, Media Streaming, Web Surfing->Internal Network->Block.
I even went as far as adding my specific devices. To block all traffic from my phone to my Windows PC, but when file sharing is turned on in Windows, I am able to browse my shared file freely from my Android device using the X-plore app.
Now this should not be possible since the firewall rule is set to totally block any data from internal device accessing other devices on the LAN. The firewall rule that allows all traffic from Internal to IPv4 should not be causing this issue since IPv4 is "the internet" and does not include file sharing services. Perhaps the X-plore app is using some strange protocol to access my network share that is bypassing the firewall?
So I found out that Windows was using port 445 for media streaming, and I added CIFS to the services in the firewall rule but the rule is still bypassed. Web filtering is set to transparent mode
This thread was automatically locked due to age.