Hi folks,
I'm not able to establish a site-to-site IPSec connection between UTM9 (BO) and my USG (HO).
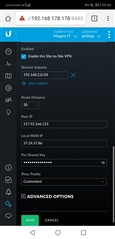
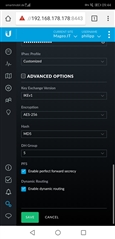
The USG is able to handle the following properties:
IKEv1, AES-256, SHA1
The Diffle Hellman Group is adjustable
The last error message at the UTM9 was:
packet from :500: ignoring informational payload, type NO_PROPOSAL_CHOSEN
Has anyone an idea which properties I must use to get the connection working?
Regards,
Philipp
This thread was automatically locked due to age.