Hello,
I've scoured through all the sophos, reddit and internet forums I can, but I'm at my wits end here.
Equipment: SG-125 (Latest Patches)
Internet Service: 1Gbps down, 50 mbps up (approximately)
Public IP Address Available: 5 total, 3 are available.
VOIP/SIP Provider : Vonage
VOIP/SIP Ports: (From Vonage business site) Vonage Business Support
The following ports are suggested for OUTGOING internet communications from the SIP device to our servers:
DNS: Port 53 UDP
TFTP: Port 21, 69, 2400 UDP
HTTP: Port 80 UDP
NTP: Port 123 UDP
SIP: Port 5060 UDP
RTP: Port 10000-30000 UDP
The following ports are needed for INCOMING and OUTGOING Internet communications from and to Vonage devices and servers.
RTP (Voice) Traffic: Ports 10000-30000 UDP.
_________________________________________
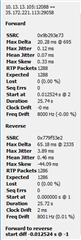
So we're not experiencing complete failure as we can receive calls, but rather the calls audio can be really glitchy, skippy, or audio will drop out completely. These phases seem to come and go with no real rhyme or reason. I'm not seeing any dropped packets, and if I run tcpdump udp portrange 10000-30000 I can see traffic is moving.
Because vonage uses DNS Naptr, I can't make firewall rules to explicitly allow the traffic through from certain IP's. Same goes for the SIP helper, which is currently disabled. I reserved all the IP's for the VOIP phones in our DHCP and made this firewall rule.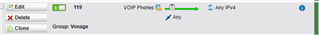
Which is far from Ideal.
In the live firewall, I see the occasional entry like this:
.137 is indeed one of our Voip phones.
IPS Is also disabled right now as part of the troubleshooting, because with it enabled, it seemed to make the situation much worse.
EDIT:
Actually, I'm seeing dropped packets
Earlier UDP entry
I have no idea where to even start with this.
This thread was automatically locked due to age.