I actually have two questions related to backend AD Authentication and web protection on a Sophos UTM 9 version 9.411-3
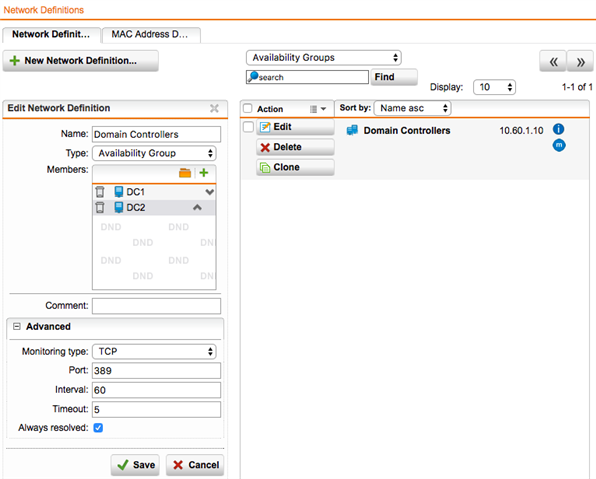
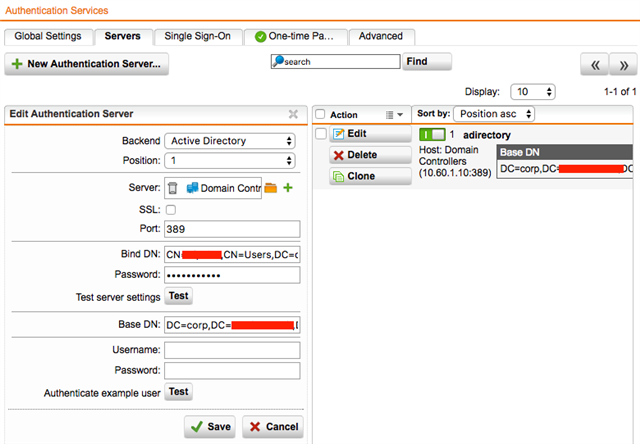
We recently had an issue with our Primary AD controller (DC1) which prevented users from authenticating and getting through the web protection. AD Authentication is required. Of course, we do have a secondary AD controller (DC2) but that was never defined in Authentication Services > Servers. I did go back into Authentication Services > Servers and I added DC2 but was not sure if that was the correct method to insure HA for backend authentication. DC1 was put back into service before I could determine if DC2 had taken over on the Sophos UTM 9. If I have two servers defined for the same domain will each be used for authentication should one fail? Is the order that they are listed important?
Second question is related to dynamic group membership (AD). I have two primary groups setup for web filtering back on the domain controllers - filtered_web_access and unlimited_web_access (for example - CN=filtered_web_access,CN=Users,DC=corp,DC=XXXXMYDOMAINXXXX,DC=com). I also have Enable AD group membership background sync checked. My question is - how do I see from the Sophos UTM point of view who is a member of those groups. I have been unable to find a GUI interface that displays that. Maybe a console command is available?
This thread was automatically locked due to age.