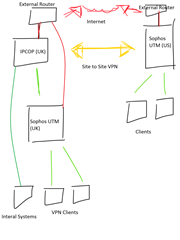
Hi all,
I'm trying to set-up routing on the Sophos UTM so it can ping a server at our US site. I can see through the tracert on the UTM that it's using the external gateway address, whereas I need it to use our internal gateway as that also hosts our site-to-site VPN.
Is there any way I can do this?
Any help would be appreciated.
Regards,
Rob
This thread was automatically locked due to age.