My first post on this Community so I hope I am in the right place. Please forgive me and tell me where I should post if I am in wrong place. I am not a network engineer so at bottom of learning curve.
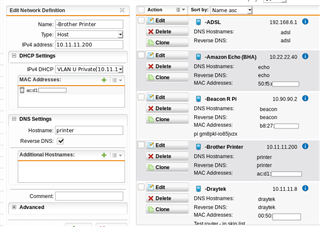
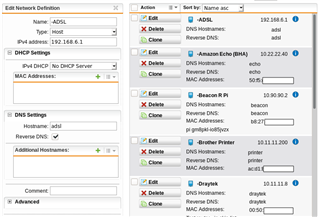
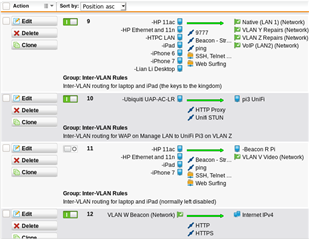
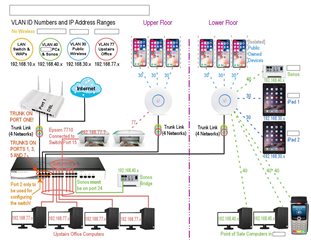
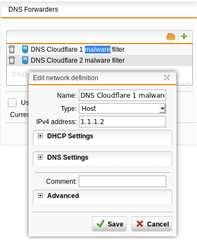
I have subnets created on sg135 UTM with DHCP on the device. I have excluded the first 20 addresses of the subnet because a number of the devices on the subnet use fixed IPs. I am having trouble with DNS on these devices and think my configuration is not quite correct. How should I define the fixed IPs in the UTM so that these fixed IP devices to ensure dns is working. I do not have a DNS on my client devices.
This thread was automatically locked due to age.