Hey Guys,
I bought my first L3 switch and was hoping to use it for vlan routing rather than Sophos UTM.
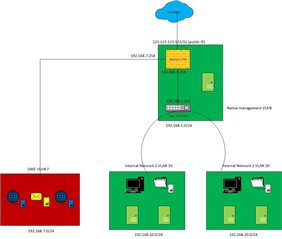
This's pretty much my network and what I'm trying to achive:
I have Sophos UTM in management vlan along with the L3 switch. Sophos UTM has 3 interfaces, 1 for WAN, 2 for LAN (management), 3 for DMZ
Both vlan 20 and vlan 30 are able to communicate to each other through the L3 switch however they are not able to go outside to Sophos UTM in management vlan or internet. Same any other device in managment or DMZ even can't reach these 2 vlans in L3 switch.
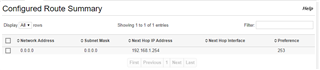
From the L3 switch I have a static route 0.0.0.0 0.0.0.0 192.168.7.254 (DMZ gateway). For some reason can't use 192.168.1.254 which's Sophos UTM IP in management. If I try to use 192.168.1.254 I get an error from the switch "The next hop ip address cannot be in the same subnet as the service/network port". I guess either the switch or Sophos have to be in a different subnet hence I'm using DMZ gateway IP just for testing. From the firewall I have set the any any deny to any any allow and put it on top just for testing.
I'm using a trunk port that Sophos is connected to. I tried creating a static route in Sophos to route vlan 10 as a gateway route as 192.168.10.0/24 > 192.168.10.254 but doesn't help.
Can someone please help with this one?
Cheers
Mo
This thread was automatically locked due to age.