Hello,
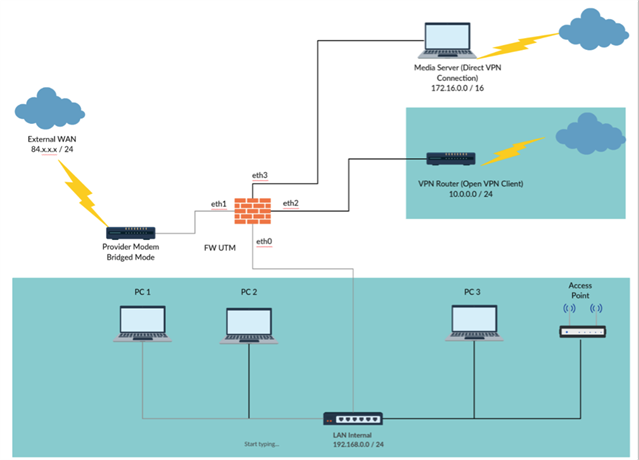
i have actual the configuration, that my media server (Win 10 with 1 Gigabit Interface) on eth 3 is in the DMZ with Network 172.16.0.0 /16. The Media Server connect directly to Internet via OpenVPN. From Internal LAN I can connect via RDP and Plex Player to the Media Server, works fine.
I have now installed on the media server virtual box, virtualized this media server to VM Guest and installed a second Guest with a Linux Gateway Solution.
Windows 10 Host Configuration:
172.16.0.2
255.255.0.0
172.16.0.1 (UTM GW)
172.16.0.1 (UTM DNS)
Windows 10 Guest VM
Adapter 1 : Bridged (172.16.0.3 / 16 no Gateway no DNS)
Adapter 2: Internal Network: Transfer
10.152.x.12
255.255.192.0
GW 10.152.x.10
DNS 10.152.x.10
Linux Gateway Guest
Adapter 1: NAT
Adapter 2: Internal Network: Transfer
10.152.x.10
255.255.192.0
10.152.x.10
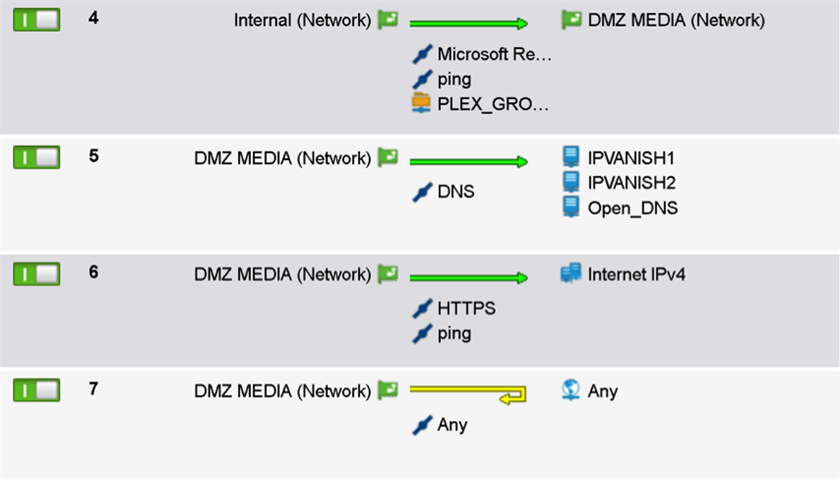
I have for this DMZ Network the following Firewall Rules on the UTM:
Intrusion Prevention local Networks – 172.16.0.0 / 16 is enabled:
Now my question is, how can I protect the Virtual Guests in the DMZ? The Guests have network 10.152.x.x but this networks / or the ip addresses in this range are not created on the UTM. Would it made sense to create this as Network Hosts, to also specific enable intrusion prevention, waf etc for them, and set specific firewall rules what are allowing just specific services / ports from Guest 1 to Guest 2?
Thx
Sally
This thread was automatically locked due to age.