Hi,
Previous IT setup the sophos (SDG135) to use LAN Proxy server in there workstation/devices when connected.
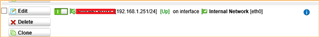
He setup an interface additional address on Internal Network using 192.168.1.251.
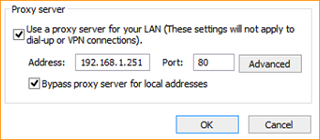
Now all connected devices must put this IP in their Internet Option Proxy Server so they can connect to the internet.
We want to know how to disable this so that they can connect directly to internet by just assigning them IP (No DHCP server, using static IP on all workstations).
We tried to disable/delete the additional address he created. using tracert, the 192.168.1.1 become unreachable. Maybe there some sort of cache I need to clear first.
DNS resolution is working properly. apps and browser can't connect to internet.
Thanks,
This thread was automatically locked due to age.