Hello everybody,
quite a lot of the ransomware incidents occurring have begun with some person receiving a legitimate-looking email which had an MS Office document as it's attachment. The document contained some macro code which started to execute upon opening the document and maybe allowing macro code execution. And fate began ....
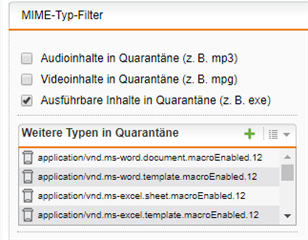
What we Need to do fro a couple of our customers is to provide configuration within their UTM9 Systems to block MS Office files which contain macros and move them to quarantine. This must work safely and must not miss any macros.
Has anybody of you been doing this before? I've been looking for configuration Options in order to get this accomplished but I've found nothing.
Seems incredible to me and I just can't belive there is really no way to esablish thsi Kind of mail security with a Universal Threat Management System like Sophos/Astaro UTM9.
Kind regards,
Axel
This thread was automatically locked due to age.