Hello,
Using exchange 2010
2x Rx connectors
- internal network
- gateway, anonymous permissions only.
All users use Outlook, some users work from home, most users have email on their phones. Occasionally I use OWA from the outside world.
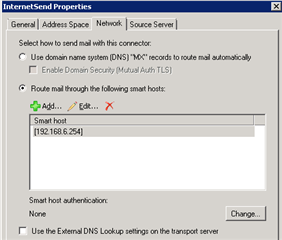
UTM SGxxx, configured for smtp proxy, no ISP smart host
There is one website with a user enquiry form.
I have no test environment so I am loath to poke around too much.
Questions:
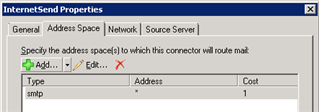
Does exchange need the UTM nominated as a smart host and Why?
Does the UTM need to accept smtp auth from the internet for the outlook services described above?
- if No? how do I turn it off (this question arises due to around 7 regular "Too many failed logins from xxx for facility smtp, blocked for 24hrs") but still allow the website enquiry form to pass.
Cheers
This thread was automatically locked due to age.