Hello
I am running the latest version utm 9.411-3 at home and I have tried all sorts of tricks to get my scenario to work. I have a CCTV NVR _network video recorder_ and some wifi cameras that I want to block them from getting to the internet totally. But I want to have access to them when I am on the local network at home or signed into the VPN and access them from outside the network.
So far I have set the cameras and NVR to static IP.
Then I added them to the exclusion list in the web proxy list so I can bypass the proxy and use the firewall to control them.
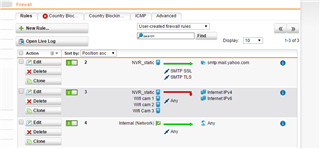
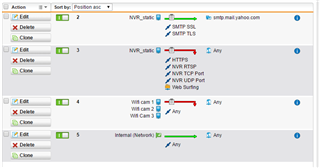
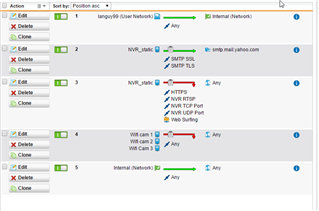
In the firewall I set a rules
devices_nvr/cam_ -> any -> Internal_network_/vpn pool -> allow
Devices -> any -> any-> reject
Internal network -> any -> any -> allow
The devices are not accessible from the internet anymore _good_ but when I try to access them after VPN into the network, they are still not accessible.
I also tried to set up a SNAT rule from VPN pool ->any->any
Source translate -> internal _address_
But it still does not work. Any advice would be appreciated.
This thread was automatically locked due to age.