Hi Guys,
So I have been reading/trying many things to get RDG to work with Sophos UTM WAF. I tried all possible combinations that I can think of however no luck. I know Sophos doesn't support RDG beyond 2008 but I saw other people posts that they successfully got it to work. I have followed their steps but still no luck. If I use DNAT it works perfectly fine but I don't want to use DNAT for security reasons.
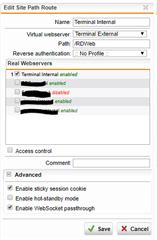
So far I'm able to get to the portal but when I get to lunch a RemoteApp or using Remote Desktop Gateway service it won't find the gateway server and I can see some errors in the logs which I couldn't figure out how to fix.
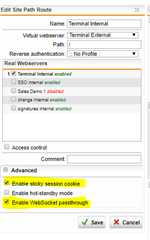
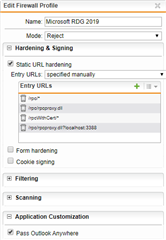
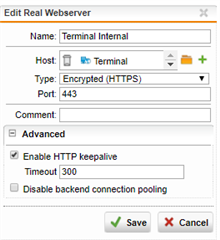
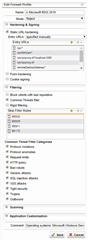
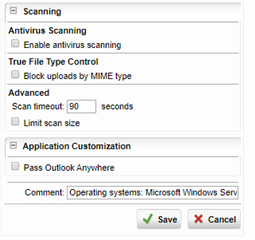
What I have setup in the firewall profile:
- Mode: Reject
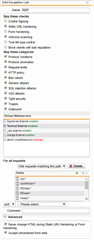
- Static URL hardening with these entries: /rpc - /rdweb - /RDWeb - /rpcWithCert - /rpc/rpcproxy.dll?localhost:3388 (I tried with "*" as well)
- Pass Outlook Anywhere enabled
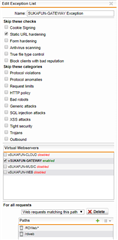
In the firewall profile exceptions:
- Static URL hardening with these entries: /rpc* - /rdweb* - /RDWeb* - /rpcWithCert*
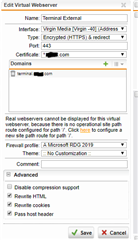
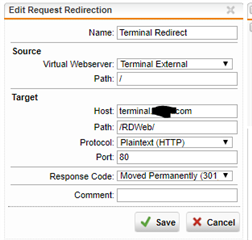
I also tried adding /remoteDesktopGateway in both. Pass host header is enabled in the virtual server. These are the errors I see in WAF logs:
2019:11:01-00:01:52 sukafun-utm httpd: id="0299" srcip="49.196.174.232" localip="139.xxx.62.91" size="230" user="-" host="49.196.174.232" method="RDG_OUT_DATA" statuscode="403" reason="url hardening" extra="No signature found" exceptions="-" time="640" url="/remoteDesktopGateway/" server="GATEWAY.MYDOMAIN.com" port="443" query="" referer="-" cookie="-" set-cookie="-" websocket_scheme="-" websocket_protocol="-" websocket_key="SQbVmEwoeogs4R/P96wrOg==" websocket_version="13" uid="XbsFcIvYPlsAALrKAZsAAAAF"
2019:11:01-00:01:53 sukafun-utm httpd: id="0299" srcip="49.196.174.232" localip="139.xxx.62.91" size="13" user="-" host="49.196.174.232" method="RPC_IN_DATA" statuscode="401" reason="-" extra="-" exceptions="SkipURLHardening" time="26890" url="/rpc/rpcproxy.dll" server="GATEWAY.MYDOMAIN.com" port="443" query="?localhost:3388" referer="-" cookie="-" set-cookie="-" websocket_scheme="-" websocket_protocol="-" websocket_key="-" websocket_version="-" uid="XbsFcYvYPlsAALrKAZwAAAAJ"
2019:11:01-00:01:53 sukafun-utm httpd: id="0299" srcip="49.196.174.232" localip="139.xxx.62.91" size="13" user="-" host="49.196.174.232" method="RPC_OUT_DATA" statuscode="401" reason="-" extra="-" exceptions="SkipURLHardening" time="25989" url="/rpc/rpcproxy.dll" server="GATEWAY.MYDOMAIN.com" port="443" query="?localhost:3388" referer="-" cookie="-" set-cookie="-" websocket_scheme="-" websocket_protocol="-" websocket_key="-" websocket_version="-" uid="XbsFcYvYPlsAALrKAZ4AAAAH"
2019:11:01-00:01:53 sukafun-utm httpd[47818]: [proxy_msrpc:error] [pid 47818:tid 4068727664] [client 49.196.174.232:36281] RPC_OUT_DATA: server 192.168.1.66:443 (GATEWAY.MYDOMAIN.com) did not accept initial PDU (HTTP status code 302)
2019:11:01-00:01:53 sukafun-utm httpd[47818]: [proxy_msrpc:error] [pid 47818:tid 4051942256] [client 49.196.174.232:36280] RPC_IN_DATA: Failed to sync Outlook Session 5a1ad305-aa9e-dd91-f2be-3de5b769d9fe: 2
2019:11:01-00:01:53 sukafun-utm httpd: id="0299" srcip="49.196.174.232" localip="139.xxx.62.91" size="155" user="-" host="49.196.174.232" method="RPC_OUT_DATA" statuscode="302" reason="-" extra="-" exceptions="SkipURLHardening" time="10175" url="/rpc/rpcproxy.dll" server="GATEWAY.MYDOMAIN.com" port="443" query="?localhost:3388" referer="-" cookie="-" set-cookie="-" websocket_scheme="-" websocket_protocol="-" websocket_key="-" websocket_version="-" uid="XbsFcYvYPlsAALrKAZ8AAAAH"
2019:11:01-00:01:53 sukafun-utm httpd[47818]: [proxy_msrpc:error] [pid 47818:tid 4051942256] [client 49.196.174.232:36280] RPC_IN_DATA: The registered Outlook Session 5a1ad305-aa9e-dd91-f2be-3de5b769d9fe is in unexpected state 'BROKEN'
2019:11:01-00:01:53 sukafun-utm httpd: id="0299" srcip="49.196.174.232" localip="139.xxx.62.91" size="0" user="-" host="49.196.174.232" method="RPC_IN_DATA" statuscode="200" reason="-" extra="-" exceptions="SkipURLHardening" time="396921" url="/rpc/rpcproxy.dll" server="GATEWAY.MYDOMAIN.com" port="443" query="?localhost:3388" referer="-" cookie="-" set-cookie="-" websocket_scheme="-" websocket_protocol="-" websocket_key="-" websocket_version="-" uid="XbsFcYvYPlsAALrKAZ0AAAAJ"
I appreciate if anyone can help me with this one.
Cheers
Mo
This thread was automatically locked due to age.