I have a very basic setup: Some of our employees use VPN to access our network from outside. For this I've setup SSL VPN as follows:
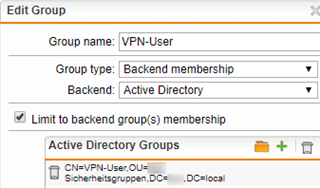
I have added our domain controller (under Authentication Services > Servers) and added an OU from active directory that is allowed to use VPN (no problem here, I just sync'd the OU again and it fetched new users):
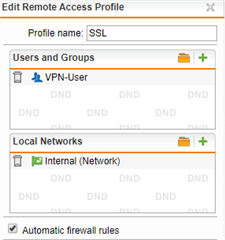
I have then created a remote access profile with the OU as users and our internal network as local network:
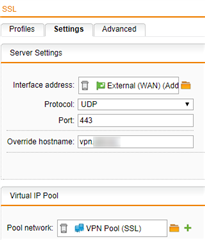
Here are the SSL VPN settings, nothing here should be a problem though since I can connect and get an IP from the SSL VPN Pool:
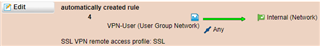
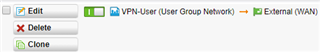
Here's the automatically created firewall rule from the remote access profile:
I've added a Masquerading rule as well but that shouldn't be necessary to access local resources:
Now my problem: I can connect just fine and get assigned a correct IP address but I cannot access anything. Tried http, rdp, icmp, etc with local resources. I'm completely isolated from the network.
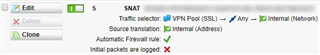
The only way I can make this work and access my network is by adding an SNAT rule that translates the SSL VPN traffic source to the internal IP address of my UTM. Notice how I'm using the SSL VPN IP pool and not the user group network (it didn't work with that):
This thread was automatically locked due to age.