I have a number of IPsec tunnels between our various Sophos UTM appliances and Google Cloud VPCs. They all seem to experience issues from time to time that causes a "Renegotiation Failure" on the Google Side but everything looks great (green) on all Sophos UTM SAs. I continually have to login to the Sophos and disable/reenable the Tunnel to reestablish the SAs. Just prior to the renegotiation failure I see the following log entries in StackDriver related to that tunnel ...
D creating rekey job for CHILD_SA ESP/0x14fc06b6/REDACTED-GCP-GW D handling HA CHILD_SA vpn_REDACTED-SOPHOS-GW{1868} REDACTED-GCP-SUBNET === REDACTED-SOPHOS-SUBNET (segment in: 1, out: 1) I CHILD_SA vpn_REDACTED-SOPHOS-GW{1868} established with SPIs 604104f6_i 9a27541a_o and TS REDACTED-GCP-SUBNET === REDACTED-SOPHOS-SUBNET
Times three (one for each Sophos Subnet)
D received DELETE for ESP CHILD_SA with SPI 537e166a I closing CHILD_SA vpn_REDACTED-SOPHOS-GW{1865} with SPIs 14fc06b6_i (0 bytes) 537e166a_o (0 bytes) and TS REDACTED-GCP-SUBNET === REDACTED-SOPHOS-SUBNET
Times three (one for each Sophos Subnet)
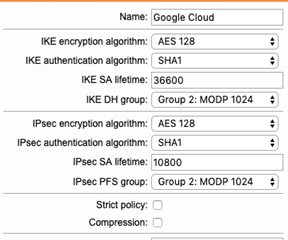
So - it appears that there was a REKEY request and then the DELETE request but once that last round of DELETE requests completed the tunnel was down (just on the GCP side - all is green on the Sophos side). I had initially looked closely at the lifetimes in the Google Cloud Policy and adjusted to what has been suggested by Google (see attached). Specifically IKA SA Lifetime should be 36600 and IPsec Lifetime should be 10800.
The remote Gateway:
And finally the Tunnel:
On the Google Cloud Side I simply created a "route-based" IKEv1 tunnel and added one subnet on the GCP side connected to 3 subnets on the Sophos side. I did it this way because Sophos UTM-9 does NOT support IKEv2 (assuming so - never found a definitive answer on that subject) and Google Cloud only allows a single remote subnet for Policy-based IKEv1 tunnels.
Is anyone else in this forum seeing anything similar or is there a better way to configure these tunnels so that they are more reliable. I never have any issues with Sophos to Sophos IPsec tunnels nor any of my AWS tunnels. Seems only to be an issue with GCP.
This thread was automatically locked due to age.