Hi folks,
sorry for my english but I hope you will understand what I want to tell you... ;)
If you've been dismayed that sophos doesn't allow you to use DNS-over-HTTPS, you've come to the right place. I was similar, but I didn't want to use another firewall solution like pfsense which would give you that by its own, so I want to find a way to continue using Sophos, but with the possibility of a DNS-over-HTTPS solution - but not another physical appliance in my network and rack.
So I decided to use an unused SG210 Aplliance and I replaced the original CPU from there with a i5-4570S from my primary firewall (SG330 which was replaced with a Xeon e3-1230v3), also the memory was upgraded from 8 GB up to 12 GB.
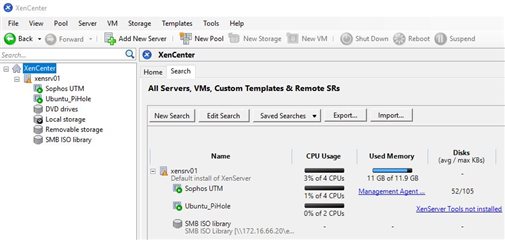
On this SG210 I have installed a Xen Hypervisor Server then - one NIC for management to administrate it on my PC with XenCenter.
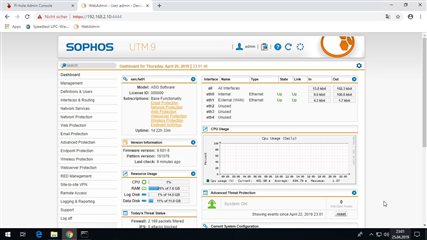
Further I installed one VM for Sophos UTM (4 cores, 8GB RAM, 40GB vhd and 5 vNICs (directly connected to 5 physical ports)).
The next step was to install a second VM with a Ubuntu Server (2 cores, 2GB RAM, 10GB vhd and 1 vNIC which is virtually connected to the physically LAN Port0 for "internal" traffic - it would also be possible to add multiple Ports to that appliance to serve further networks attached and placed on sophos utm).
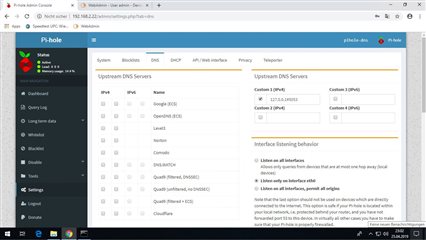
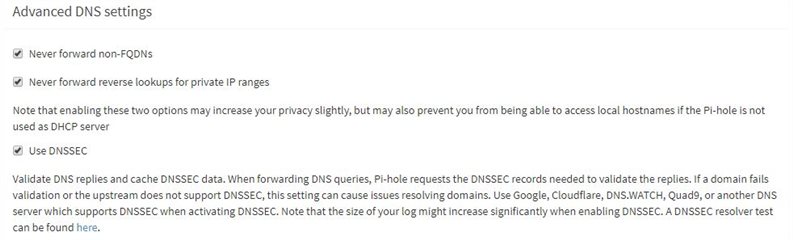
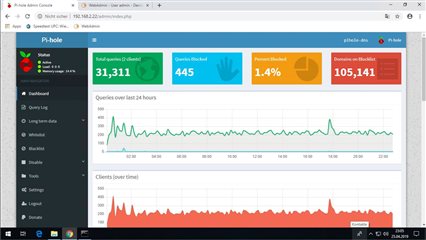
This Linux VM was configured as PiHole DNS and also installed the cloudflared DNS Proxy plugin (https://docs.pi-hole.net/guides/dns-over-https/) and configured all like described in the link and docs attached.
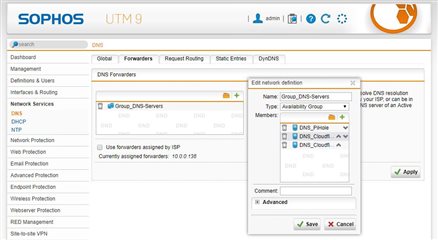
On the Sophos UTM I configured a DNS forwarder and added a DNS Group for this; primary the PiHole and then Cloudflare public DNS - if the pihole would not be reachable.
So I have the Sophos as DNS via DHCP for internal traffic and for external it will be forwarded to the PiHole Cloudflares...
The Xen Server was configured to autostart the VMs on reboot or failure.
At the moment I have attached four VMs to the sophos which are running on my PC here also one WLAN AccessPoint. To surf with my mobile phone and tablet.
All works fine and quick - internal and external. Fast response and full ISP Througput / bandwidth with all acitivated features like web filter, av proxy, IPS ... the CPU usage then is about 20%.
Please don't tear up the concept as such - it should only be a rough guide and a possibility test. Details can certainly be better implemented or optimized - my first concern here was whether a Xen Server is executable on the SG and how the whole thing behaves in practice in terms of stability and performance or functionality.
So what I also want to say is that you can use smaller devices like all the chinese aplliances which are placed in your living rooms - the totally silence boxes ;)
I think 4GB for sophos utm, 1GB for PiHole and 1-2GB for Xen would be enpough - so an ammount of 8GB for the physical "Xen Appliance" would be enough.
 4186.Ubuntu PiHole DNS over HTTPS Installation.pdf
4186.Ubuntu PiHole DNS over HTTPS Installation.pdf
2350.XenServer AutoStart VMs.pdf
This thread was automatically locked due to age.