I have country blocking enabled and find that I can't use some tools.
I have installed and running a v9.510-5.
When viewing the live log, I see some entries indicating a "Country blocked" for IP addresses which GEOLOCATE shows as being in the US, which is not blocked.
example:
11:26:02 Country blocked TCP 192.168.0.58 : 57769→35.201.70.64 : 443 [SYN] len=60 ttl=63 tos=0x00 srcmac=a4:08:ea:28:6a:31 dstmac=34:97:f6:27:76:9f
All IP location tools I've tried indicate 32.201.70.64 as "Mountain view, CA"
I have "United States" set to "OFF" in the firewall Country Blocking tab, so why is this IP being blocked?
I also tried adding an exception as shown below, but this did not work. Am I doing it incorrectly?
Also, I tried adding an "exception" for this IP address, and this does not seem to work. I added a "host" exception with the 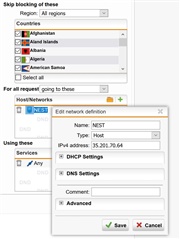
This thread was automatically locked due to age.

