I have just installed UTM 9 on my home network.
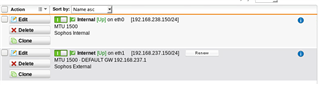
Interfaces configured as below
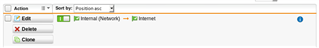
I have configured NAT Masq as below
From my "Internal" network I have no problems accessing machines on the internal network, or on the "Internet" interface ( even hosts on the internet as the G/W for my "Internet" interface is my cable modem).
From my "Internet" network I am unable to access any host on the "Internal" network.
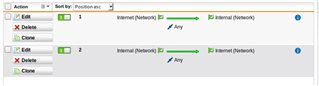
I have created an open rule as below - but I still can't access by "Internal" hosts from the "Internet" network
Any ideas on why I might be missing?
David
This thread was automatically locked due to age.