Hello,
I have an issue with the following setup:
- 1x Sophos SG125w an 2x AP 55C
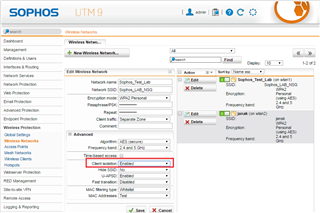
- 1 internal network (192.168.30.0/24) with the interfaces eth0, eth2, eth4-7 and wlan1-4 bridged into it. wlan 1 is radiated by SG125w and both APs, while wlan2-4 are radiated by only one of the hardware devices. The two APs have an IP from that internal network (192.168.30.253 and 192.168.30.252, 192.168.30.254 is the SG125w). wlan1-4 are bridged into AP LAN.
- 1 guest network which has its own interface on the SG125w but this a virtual interface. There is no bridge on this interface. Guest network is wlan0 and it is a seperated zone.
- Standard Proxy is on for the internal network, it is not configured for the guest network. Under Web Protection -> Filtering Options -> Transparent Mode Skip List the internal network is listed under Destinations, the checkbox "Allow HTTP/S traffice for listed hosts/nets" is unticked.
- One Firewall Rule allowing Guest network->any service->Any IP address.
A client from the guest network can now connect network drives and access data on the internal network if the user puts in the right credentials. This was not the plan but I don't see the mistake in my configuration. If the client would have a VPN connection into the internal network then it should work (it does), but without there should be no accesebility from the guest network to the internal network.
Pleas help!
Regards
Tim
This thread was automatically locked due to age.