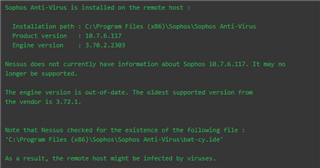
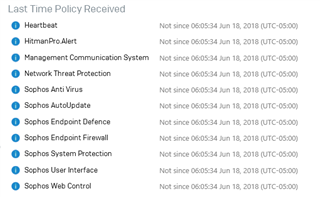
Our vulnerability scans are showing all our servers are out of date on AV. Below is the output of the scan as well as what the server is showing. Of course everything is green on Central. Another day another day of trying to figure out what Sophos has broke.
This thread was automatically locked due to age.