Hey Folks,
I am new to SafeGuard so please... be gentle [;)]
So I have my server up, running, and functioning. My test client is pulling policies and reporting back to the server. It's encrypted the non-boot volume (there are 2 volumes on this drive, 1 for the OS, and 1 for Data for easy OS wiping), but it simply will NOT encrypt the OS drive. I have been playing with this all day, messing with bitlocker group policies, client installation, and SafeGuard policies. I am SURE I'm missing something simple, but im not sure what it is.
Troubleshooting Steps
- Uninstallereinstalled client (including pre-reqs) and reinstalled
- Fiddled with policies and group policies
- Rebuilt my test server
Sophos Server :
- Windows Server 2012 R2
- SQL Server 2014
- Sophos Server and Management Center 7
Sophos Client :
- Windows 10 build 1511
- Sophos Client 7.02
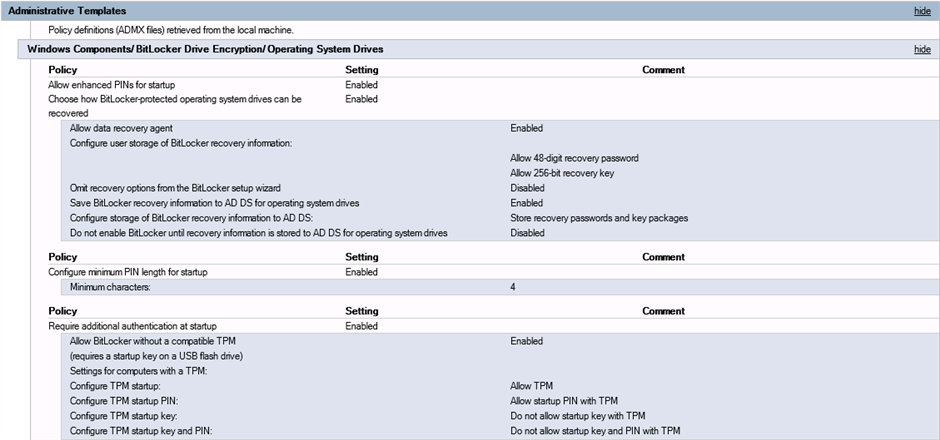
Here's the Bitlocker GP Settings :
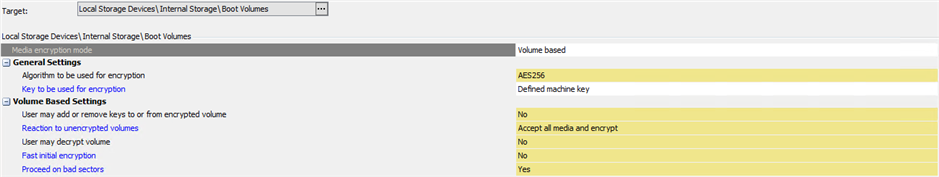
Here's the Boot Volume Policy :
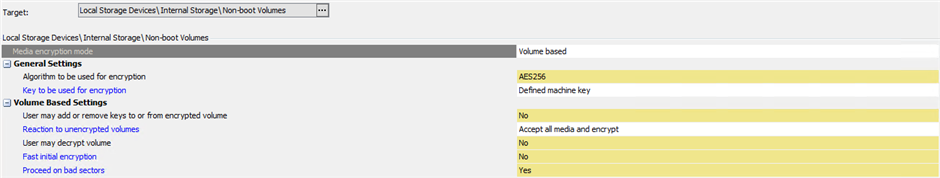
Here's the Non-Boot Volume Policy :
Any assistance would be greatly appreciated!
This thread was automatically locked due to age.