Heloo everybody,
i installed sophos safeguard version 8.10 , all components are installed correctly.
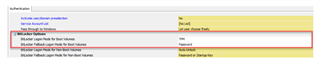
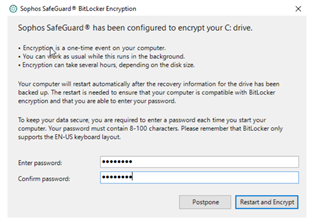
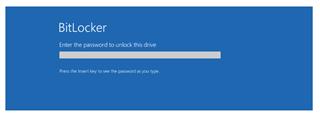
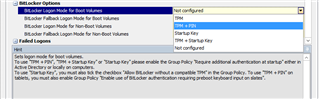
i configure two policy (device encryption) and (Bitlocker POA : for the authentication of the bios when the computer start) , when i installed the sophos client the installation has succedded , the pc start to encypt the disk at the first reboot but the problem is the screen POA don't appear to configure password for the authetication and the PC's will authenticate at the startup.
i configured this setup many time in the past and it work correctly so i am sure about the parametres of the setup.
the OS client is windows 10 pro
PC are lenevo
thank you for your help
This thread was automatically locked due to age.