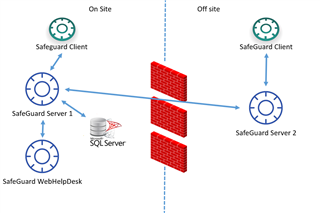
Kicking around SafeGuard Enterprise in a test environment for Synchronized Encryption.
In our production environment we will have users working remotely. Can the SafeGuard Enterprise server be set up to allow clients to sync over the Internet?
They currently use a VPN when they need to, and I know SafeGuard could sync that way, but some users could go days without ever using the VPN.
This thread was automatically locked due to age.